SELinux Enabled and No Data Transmitted
With CentOS a kernel extension Security-Enhanced Linux(SELinux) is provided and enabled per default. This extension controls access to specific resources on your system. This can include tideways-daemon access to web-service (http) data.
First, to check if SELinux is enabled run the following command:
sestatus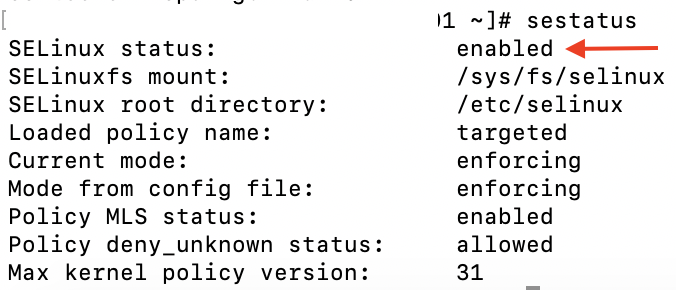
If SELinux is disabled, you can stop reading this article, because there is another reason why data not transmitted. Otherwise, please refer to the troubleshooting checklist
Generate Policy Module for the Tideways-Daemon
If SELinux status is enabled then the solution is to generate a policy module for the tideways-daemon. The policy module has to defuse the access denied from httpd_t process connect to tidewaysd.sock. To check the er, look at audit.log with:
grep tidewaysd.sock /var/log/audit/audit.logUse provided audit2allow tool to generate policy module.
First create an human readable enforcement-file type (*.te) that describes the policy type and access control:
grep tidewaysd.sock /var/log/audit/audit.log | audit2allow -m tideways-daemon > tideways-daemon.teIt is very important to verify the generated tideways-daemon.te-file with checking the allow-rules cat tideways-daemon.te:
module tideways-daemon 1.0;
require {
type httpd_t;
type initrc_t;
class unix_stream_socket connectto;
}
#============= httpd_t ==============
#!!!! The file '/run/tideways/tidewaysd.sock' is mislabeled on your system.
#!!!! Fix with $ restorecon -R -v /run/tideways/tidewaysd.sock
allow httpd_t initrc_t:unix_stream_socket connectto;
Please, reset the file context for /run/tideways/tidewaysd.sock with proposed command:
restorecon -R -v /run/tideways/tidewaysd.sockIn SELinux is the 'restorecon' -command for reseting the security context type (extended attributes) on files.
The command `audit2allow `with option -M generate the loadable module package:
grep tidewaysd.sock /var/log/audit/audit.log | audit2allow -M tideways-daemonIf it working fine, it outputs: 
Finnally, enter the suggested command to activate it:
semodule -i tideways-daemon.ppList Policy Module for the Tideways-Daemon
Per default the policy module is listed with priority 400:
ls /etc/selinux/targeted/active/modules/400Remove Policy Module for the Tideways-Daemon
semodule -r tideways-daemonIt is deleted on your system’s storage and you cannot load it again.