Azure Active Directory for Single Sign-On
| The Azure Active Directory SSO functionality is available to customers with the Pro plan. Get in contact with [email protected] to get details about the Azure Active Directory SSO feature. |
Installation
-
Log into the Azure Portal
-
Select "Azure Active Directory"
-
Under "Enterprise Applications" click "New Application". Search for "Tideways" to create the application integration for Azure Active Directory.
-
You will be redirected to the overview page of the "Tideways" application integration.
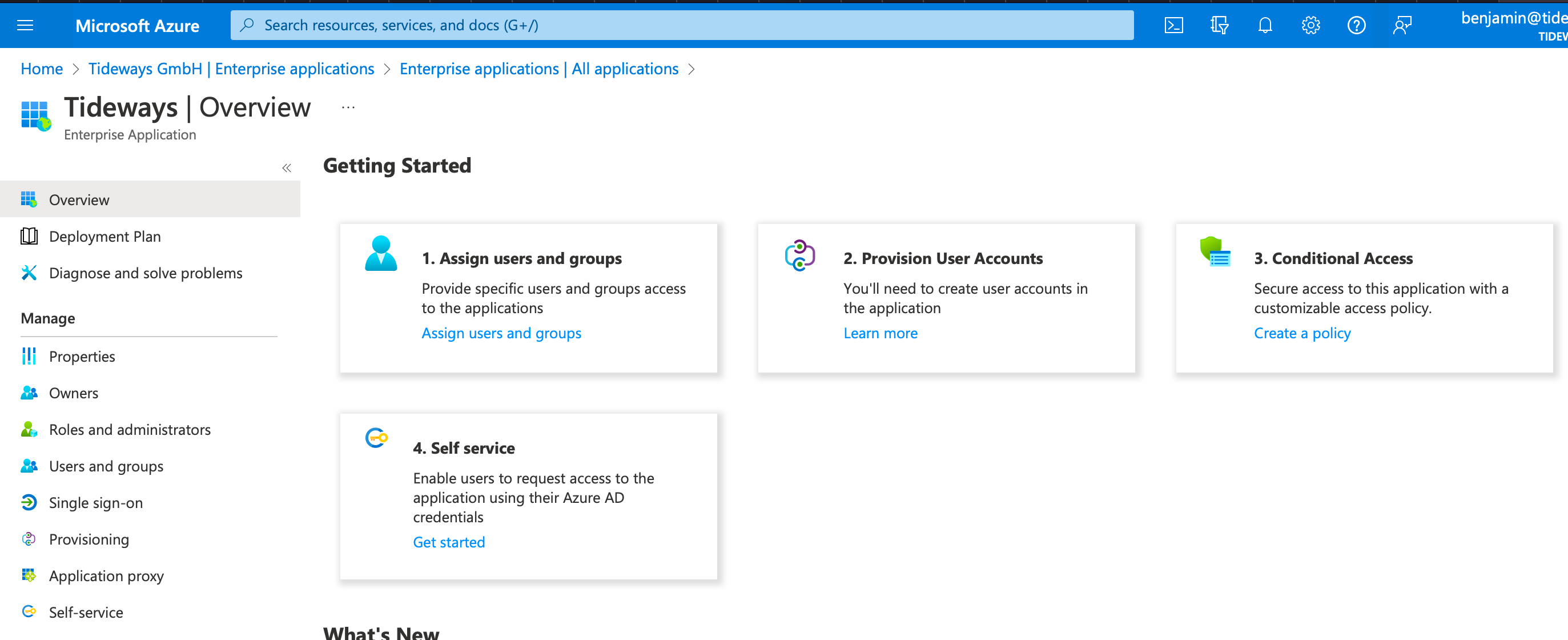
-
Select "Assign Users and Groups" and you can assign users and groups with one of three roles that map to Tideways roles:
-
User
-
Privileged
-
Administrator
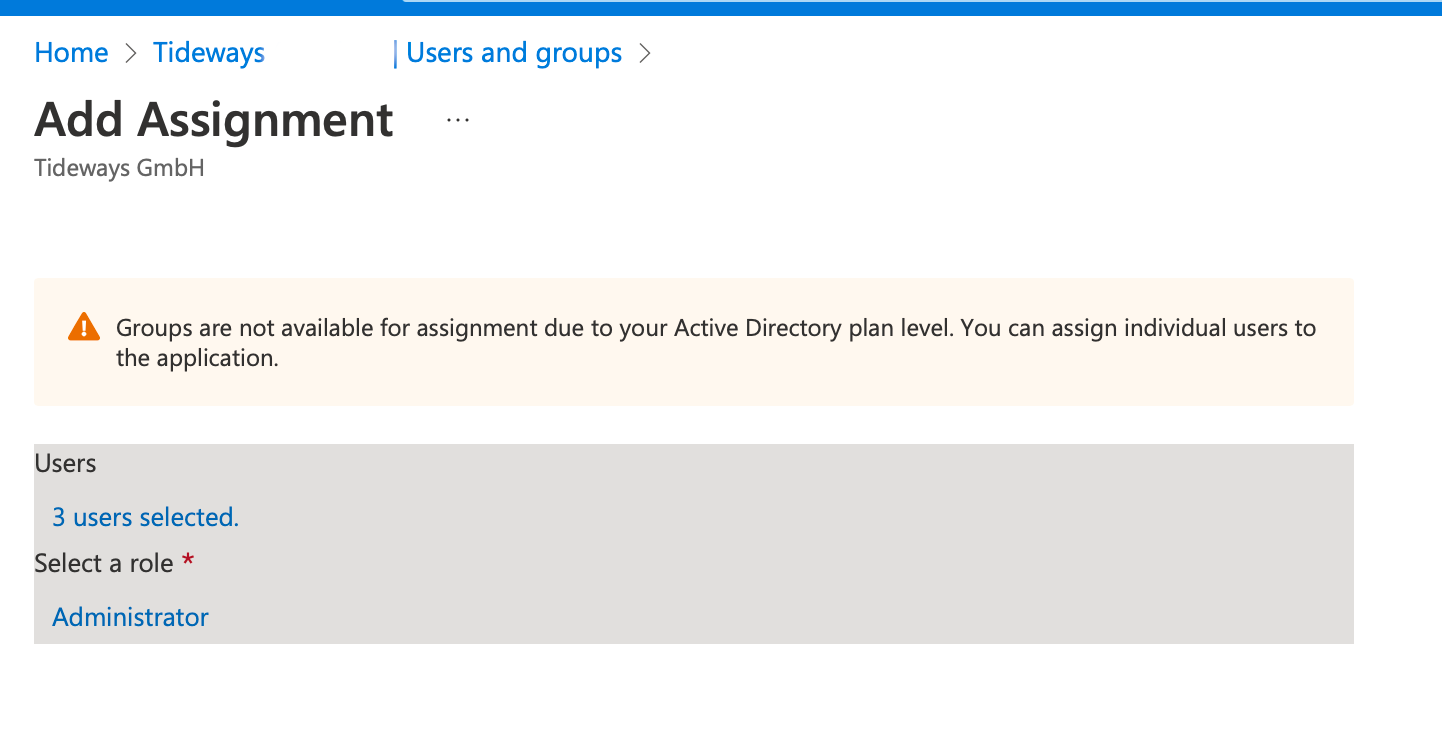
-
-
Next, the "Provision Users" action in Azure AD asks to set up the users in "Tideways" itself. This step is about creating an "Azure Active Directory" synchronization in your Tideways organization and configuring the "Tenant ID". Click "Configure Azure AD for SSO" in the Azure AD SSO settings of your Tideways organization.
You can find this in the "SSO & User Synchronization" settings screen reachable from the "Organizations" link the dropdown at the top-right:
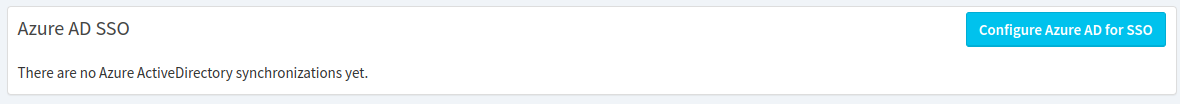
On the "Create Azure AD Synchronization" form enter a name and the Tenant ID from your Azure Active Directory. You can optionally choose a team to synchronize these users into.
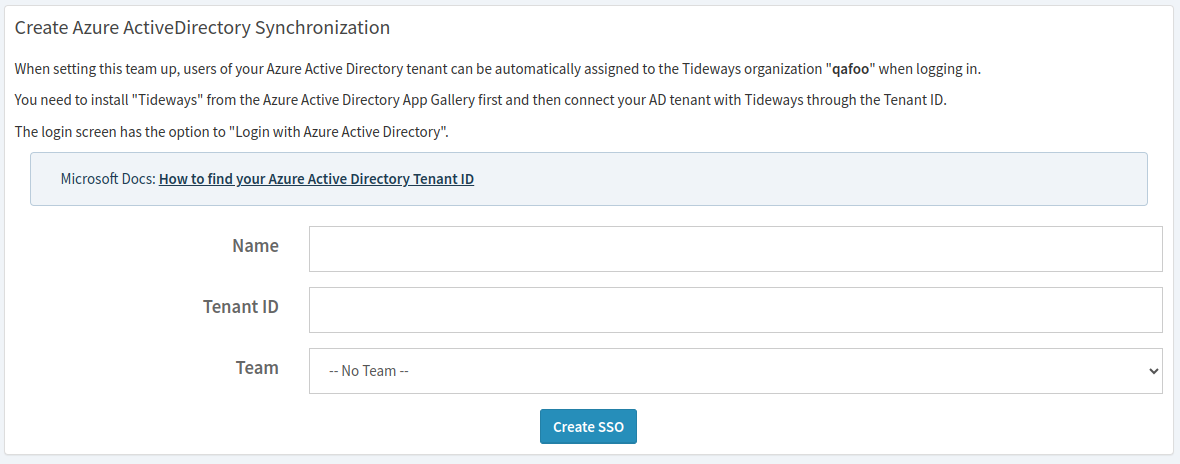
You will find the Tenant ID in the Azure Portal Active Directory configuration. See the Microsoft documentation for more information.
After saving the synchronization the Azure AD SSO functionality is setup. Assigned users can now log into Tideways from the Login screen by clicking the "Login with Microsoft Azure Active Directory" button at the bottom.
OpenId Connect Permissions
The Tideways application will be asking for consent to request the following permissions from a user logging in using Azure Active Directory:
-
openidto be able to use OpenID Connect login -
emailfor sending the weekly report, notifications and product updates/release notes to the user and connecting them to the organization when they write in via e-mail support. -
profilefor storing the firstname of the user in order to address them in notifications
User Provisioning
The Tideways Azure Active Directory integration does not support SCIM, but some rudimentary user provisioning is done by assigning users of a specific Azure AD tenant with organizations that have Azure AD Teams with the same tenant.
When a user is using "Login with Microsoft Azure Active Directory", Tideways checks if there are any organizations with the same tenant ID configured and invite them into the organization automatically.
Conversely, when a new team with an Azure Active Directory Tenant ID is created all users that are already registered in Tideways and part of the same tenant are immediately invited into the organization.
Troubleshooting
Error: User provider azure did not pass "email" information to Tideways.
The field "email" is not required to be set for a user in Azure Active Directory, instead the principal username is often the e-mail address already. Since the principal name can also be different to an email, for mapping emails to Tideways it is required to set the "email" field for users.
Azure Active Directory ensures that the e-mail address must be part of the domain that the Azure account is managing. This allows us to use the e-mail safely without validating it again.